Level of complexity: Beginners
Hello and welcome to Introduction to Azure Sentinel. If you re (relatively) new to the DevOps Universe and you re still finding your way around, you’ve come to the right place. I ll walk you through security issues you can resolve smoothly with Azure Sentinel. It is your go-to tool for when you need an immediate response to the massive increase of alarms and threats caused by constant data expansion that needs protection.
The blog is a brief overview of the powerful Azure Sentinel and it covers comparison to other Azure Cloud Security tools.
What is Azure Sentinel?
Microsoft defines Azure Sentinel (available in preview mode from Feb 2019) as a scalable, cloud-native, Security Information Event Management (SIEM) and security orchestration automated response (SOAR) solution.
In short, it is a cloud security tool that collects, analyzes, and makes automated responses possible, all by using enormous Microsoft Azure resources.
It tackles issues such as “alert fatigue” by the sheer size of events and alerts on happenings every day. Azure Sentinel uses machine learning to dig out valuable insights and provide precise context for smart decision-making. It accomplishes all of this while offering “a birds-eye view” across the organization, as Microsoft put it.
What does Azure Sentinel precisely do?
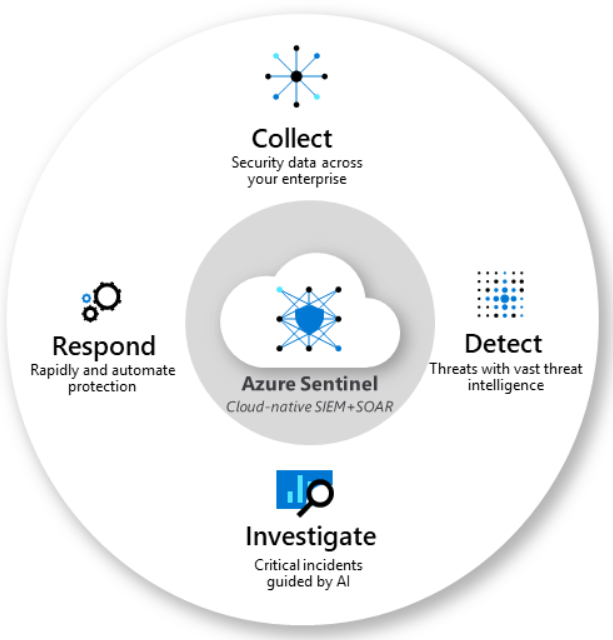
Collects: MS Azure Sentinel collects Subscription data across all users, devices, applications, and infrastructure, both on-premises and from multiple clouds. This is a starting point for making any well-informed business decisions.
Detects: MS Azure Sentinel minimizes false positives using Microsoft’s analytics and unparalleled threat intelligence, detects the usual suspects and threats even before they occur. As previously mentioned, Azure Sentinel uses ML to identify unusual behaviors and detect any changes in how users manage their resources and rights.
Investigate: The moment Azure Sentinel detects unusual behavior, it sends reports to an officer in charge, providing them with an ability to drill down events, users, and resources. In case a user attempts logging in but fails multiple times, on multiple occasions, from multiple devices, it can be rightly assumed that the account/workstation has been compromised. This exact example demonstrates the efficacy of Azure Sentinel in investigating suspicious activities and early detection of potential threats.
Responses: Built-in orchestration and automation of common tasks can help in addressing the threats early and promptly. This means that we can preconfigure actions that will be triggered if some threat appears and this can happen automatically without our intervention.
E.g. in case of an unauthorized and failed access attempt, all the intentions will be proactively and automatically blocked. These actions would then have to wait for the official review.
How is Sentinel different from other Azure Security tools?
Other Azure security tools can easily get mixed up with Sentinel and you can find yourself struggling to grasp all these entangled pieces of information. Let s shed some light on this.
Azure Security Centre vs Azure Sentinel
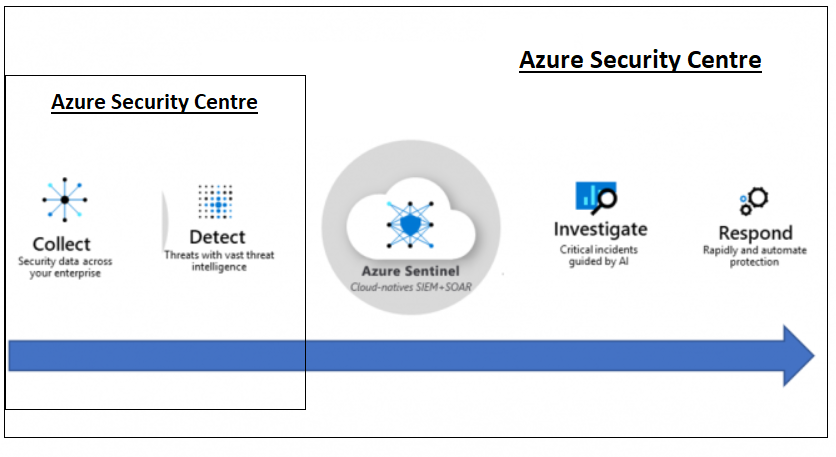
Azure Security Center is about understanding how to best configure Azure assets, while Azure Sentinel is all about hunting and detecting suspicious activities and threats.
Azure Security Centre collects and detects and Azure Sentinel uses that data source (combined with other data sources) to investigate and respond extremely rapidly to threats.
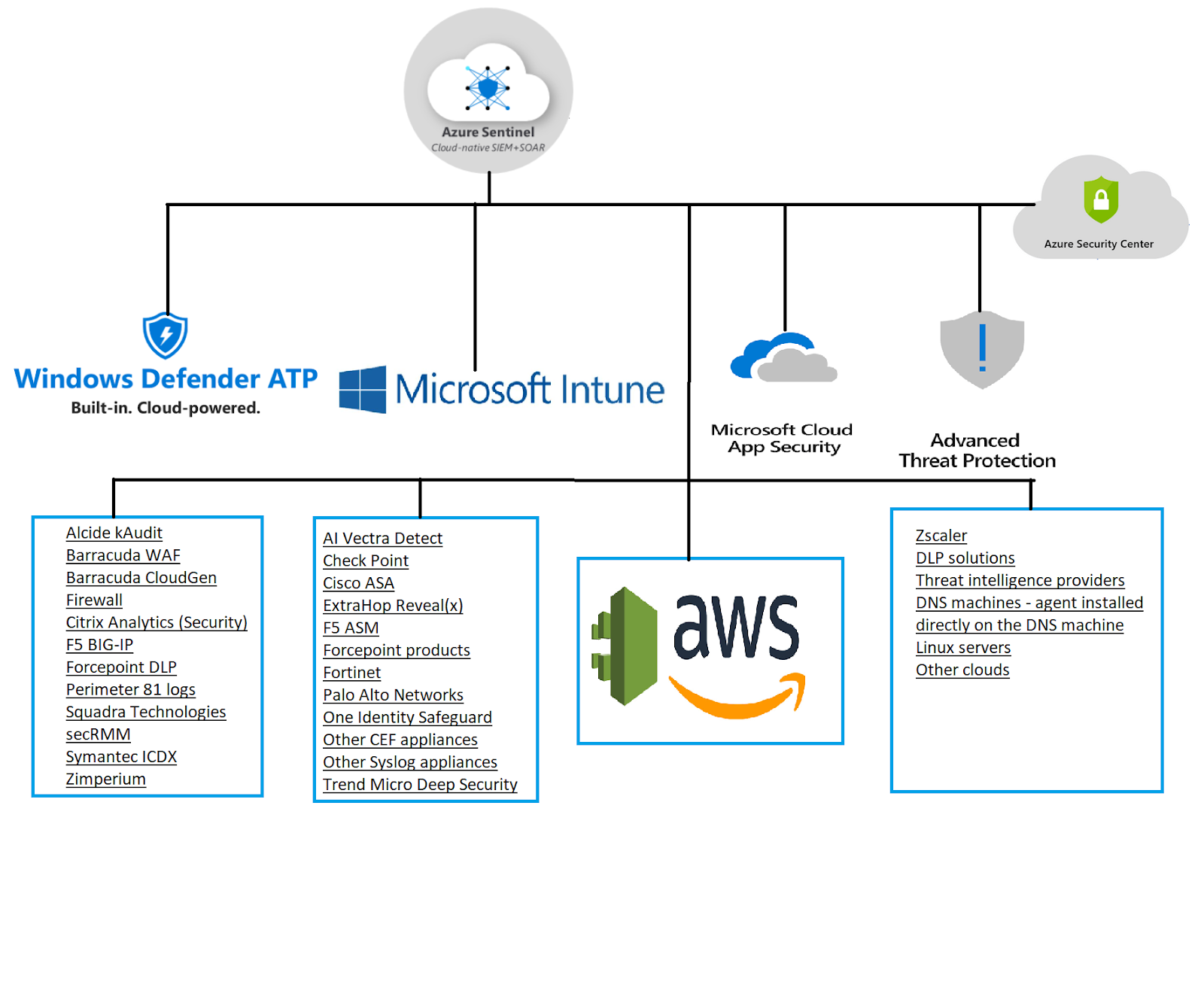
Advanced Threat Protection (ATP) helps detect and investigate advanced attacks and insider threats across the entire network.
Cloud App Security is all about protecting an environment from bad apps, compliance, information leakage protection, policy control, control and monitor shadow apps (random apps users use for non-business purposes), monitor unmanaged devices, etc.
Microsoft Intune is a cloud-based service that focuses on mobile device management (MDM) and mobile application management (MAM). It helps keep control of an organization s devices, including mobile phones, tablets, and laptops (block access to jailbreak devices, or bad mobile apps)
Microsoft Defender Advanced Threat Protection is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. It helps secure clients and sends data to logs.
All these tools are collecting and sending data, some of them are responsive, but only on a local level.
Azure Sentinel is the only one that can actually take the bull by the horns. It uses logs as a data source and provides a comprehensive overview of insights. On top of it all, Sentinel orchestrates an unparalleled response to sophisticated threats (both potential and real).
It is more than obvious that Azure Sentinel “digests” all kinds of data sources; basically, anything that supports open standard formats like Common Event Format CEF and Syslog which also able to integrate smoothly with Azure Sentinel.
Azure Sentinel Pulling Power
It is incredibly easy (almost effortless, if you ask me) to get started with Azure Sentinel; the tool is exceptionally intuitive and easy to use, taking max 10 minutes to set it all up and get it running.
In order to make the best use of everything I just mentioned, I advise you to take some time to fulfill these:
- Activate Azure Subscription;
- Log Analytics workspace (create a new one or pick an existing one); Get hold of Contributor permissions to the subscription in which Azure Sentinel workspace resides to enable Azure Sentinel;
- To use Azure Sentinel, get hold of the contributor or reader permissions on the RG that the workspace belongs to
Note
- Some data sources (in Azure Sentinel: data connectors) require specific permissions or even specific licenses.
- There are free trial versions but Azure Sentinel is a paid service. Read more about this here.
And we re ready to get going!
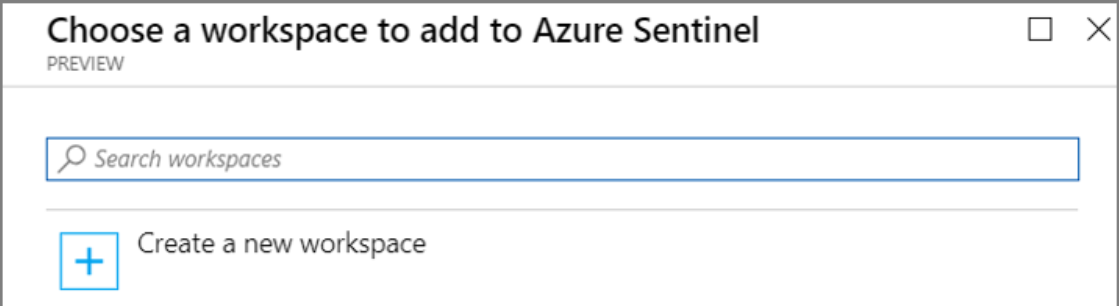
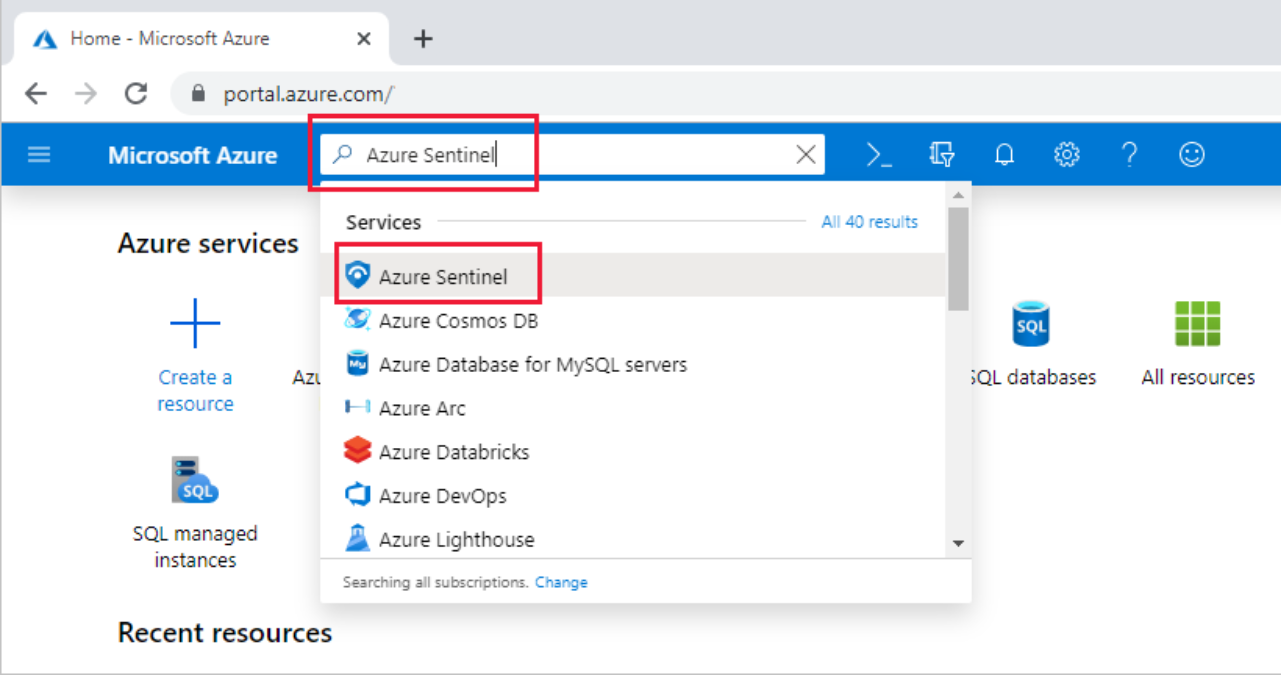
Once signed into Azure portal, select the desired subscription, search for Azure Sentinel and hit Add;
It will ask you to create new or pick the existing workspace for Sentinel:
Finally, select Add Azure Sentinel.
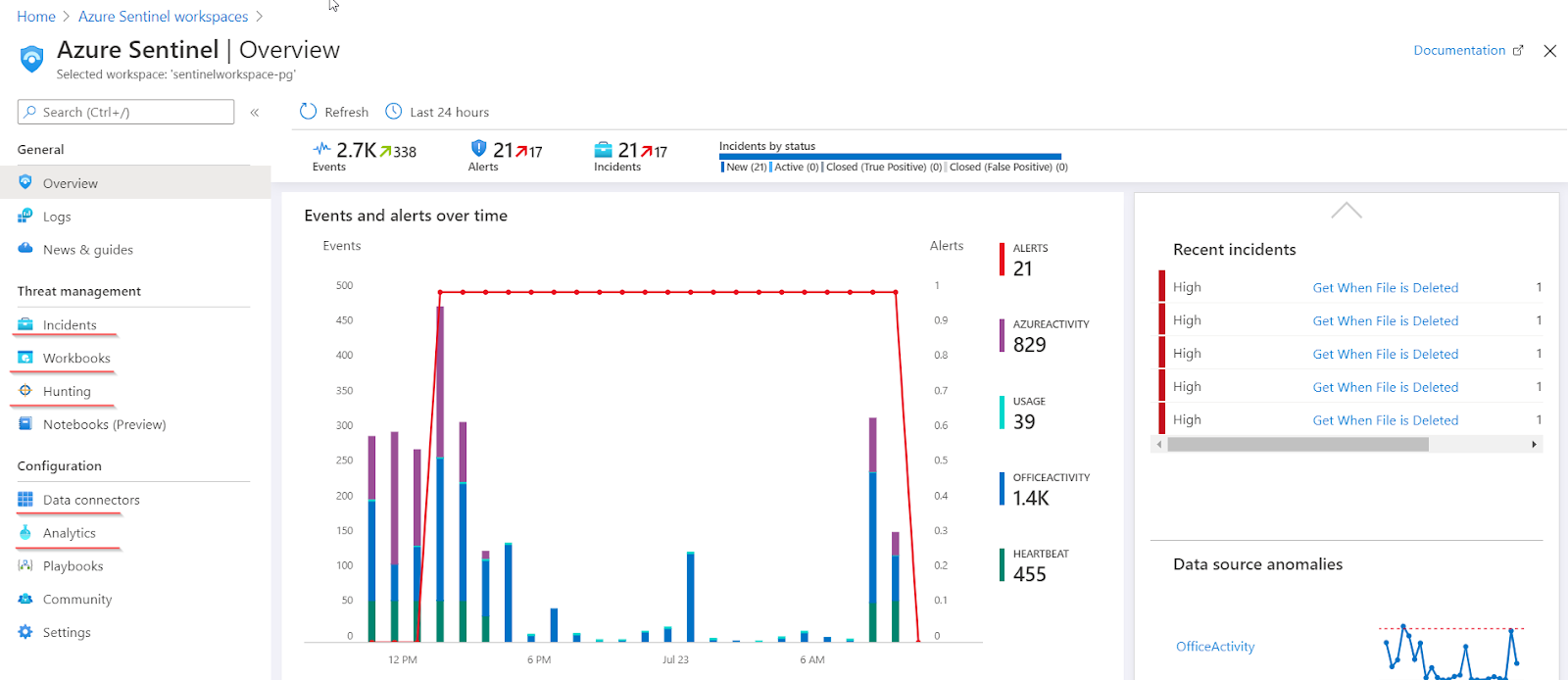
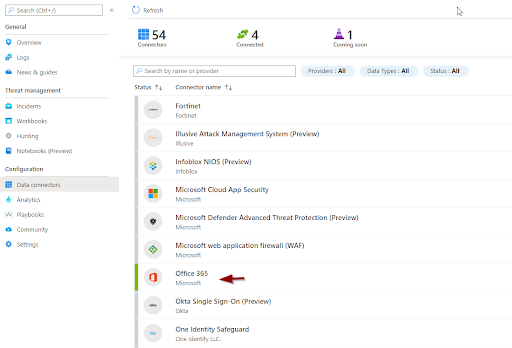
Once you open the Azure Sentinel dashboard it will be empty. You will need to collect data through Data connectors (feel free to pick Office365 and/or try any other for which licenses and permissions are available).
Now, with Data Connectors added, all the necessary data to set up Azure Sentinel is ready.
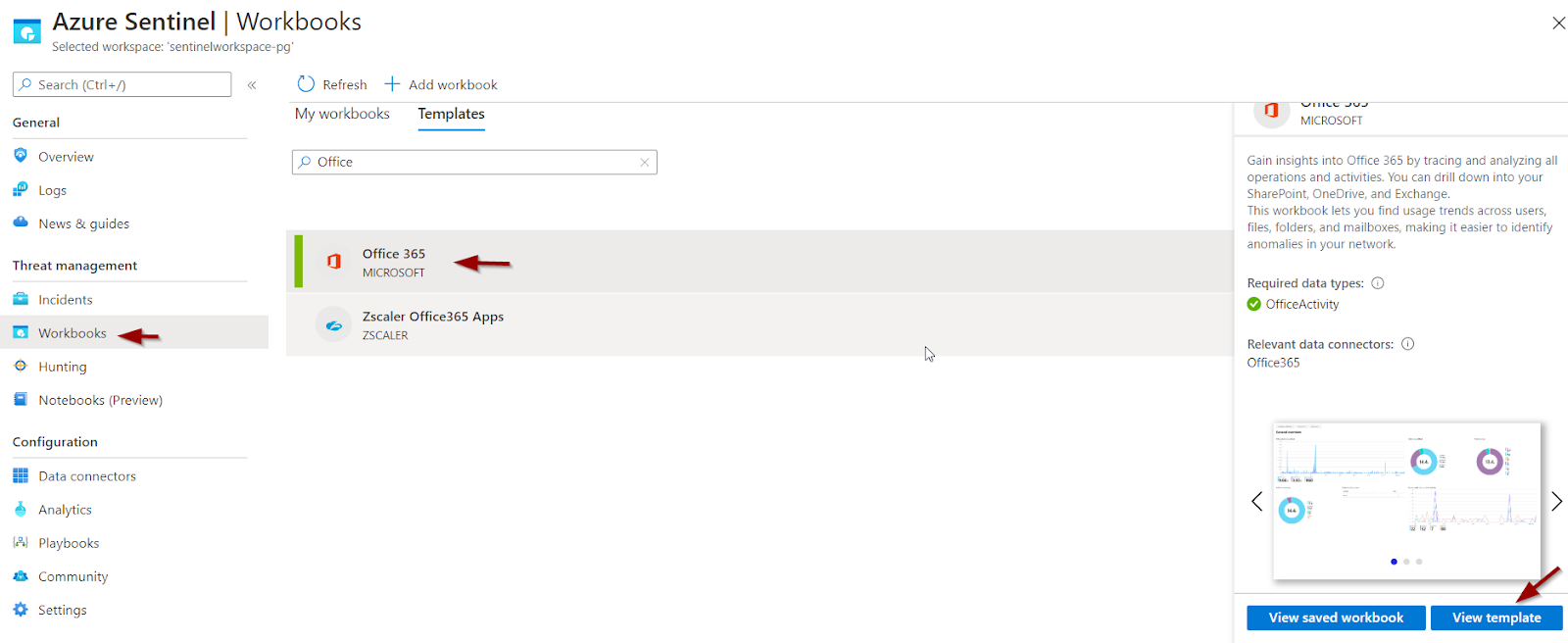
Use Workbooks to monitor and visualize the data in Azure Sentinel.
Workbooks enable creating personalized templates, but you can also use already built-in templates.
It is possible to add more than one and/or switch among them as it suits you.
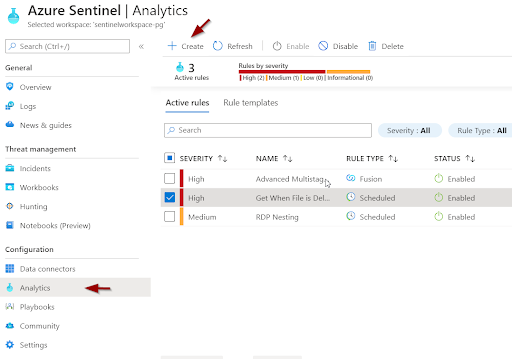
You ll notice that it s possible to monitor your data as it s being collected. Use Analytics from the Azure Sentinel dashboard to analyze data.
Notes:
There are already predefined rules for alerts (located in Rule templates), or one can create a new one by yourself. In the interest of clarity, create a simple Alert rule that further triggers Incident (you ll find a sample below);
The difference between Alert and Incident in Azure Sentinel is that Alert is a behavior needed to build an Incident, but it is not the only and mandatory tool.
E.g. If a file is deleted, and Alert rose (initially, nothing suspicious here!) only after repetition of this action within a limited time span, perhaps a minute, Azure Sentinel raises red flags!
Sample
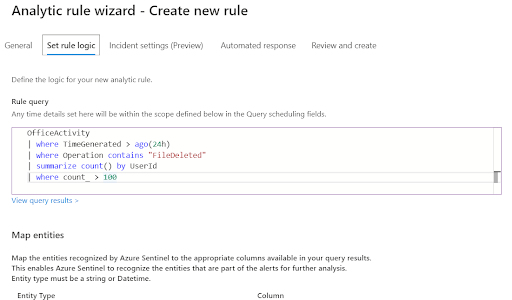
- Create a simple Alert to check for deleted files by a user, but raise an incident only if there are users with 100 or more deleted files in one day.
- Go to Analytic and then on Create and pick Scheduled query rule.
- General tab: put SampleAlert, leave other input fields as is, then go to Set rule logic and paste this query (written in Keyword Query Language (KQL)):
OfficeActivity
| where TimeGenerated > ago(24h)
| where Operation contains "FileDeleted"
| summarize count() by UserId
| where count_ > 100
| extend AccountCustomEntity = UserIdThis query will tell if any users have deleted e.g. 100 files in the last 24h.
- Fill other fields like “Run query every”;
- Leave Alert threshold as is;
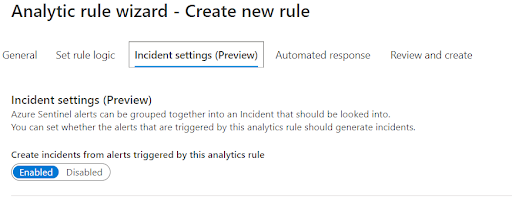
If left as it is and saved, only Alerts, not Incidents, will be created; If the Alert rule needs to rise Incident, go to the Incident setting tab, and enableCreate an Incident.
It is possible to use the “Automated response” tab to select some actions by selecting a predefined Playbook.
Azure Sentinel Playbook is a collection of procedures that can be run from Azure Sentinel in response to an Alert. Security Playbooks in Azure Sentinel are based on Azure Logic Apps, which means that they provide all the power, customizability, and built-in templates of Logic Apps.
In the end, review and create your Alert that will run incidents too.
Create a Playbook
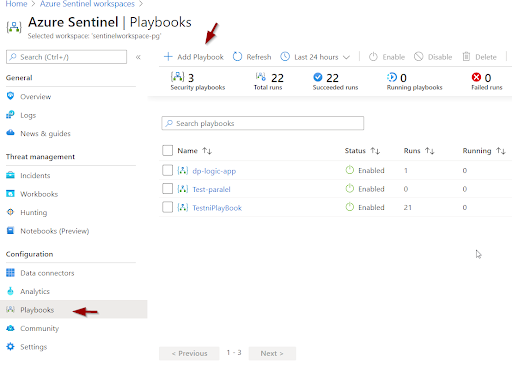
- Open Azure Sentinel dashboard
- Select Playbooks
- Add Playbook
A new Logic App window opens (see below):
- Name it
- Hit Create
Once a new Microsoft Empty Workflow window opens, it is necessary to define actions in a JSON file within it.
Recommendations to novice users
- Go back to Azure Sentinel on Playbooks;
- Click (on a newly created) Playbook;
- Once on Logic App Designer, it is possible to drag and drop actions and entities;
- Go to Blank Logic App to set up actions one wants to run when an Alert occurs;
- Click Save
Note
Azure Sentinel Dashboard Community contains and generously shares access to a massive load of predefined Workbooks, rules, playbooks, and hunting queries created by the community members.
Alert vs Incident
Incidents can be investigated and drilled down into, including insights into all the details that possibly could lead to Incidents like usernames, devices involved, IP addresses, etc.
Alert is just a triggered rule.
Note
It is worthwhile investigating an Incident in Azure Sentinel and approach it with attention to gain its utmost best.
The Hunting tool (Hunting in Azure Sentinel Dashboard) is the best option for preemptively investigating Alerts and Incidents. It is a powerful query environment with IntelliSense that enables requesting a query and saving it for later use.
If more power is needed, it is highly recommended to use a programming language like Jupyter notebooks (Notebooks in Azure Sentinel), which extends the scope of data manipulation. It combines full programmability with a huge collection of libraries for machine learning, visualization, and data analysis. With Jupyter Notebooks, visualizations and graphics, data processing and analysis, statistics and numerical computing, machine learning and deep learning are all at the disposal.
Summary
Azure Sentinel is a scalable cloud tool that detects, investigates, and responds to threats if found. It can monitor an ecosystem from cloud to on-premise, workstation, mobile devices. It is easy to use, and paid service (circa 2.20 per GB-ingested, see more about pricing here). It can receive all kinds of data sources (Amazon Cloud Trail, Firewall logs) and is using machine learning (ML) to reduce alert fatigue and to detect unusual behavior normally not detected.